Over 70% of organizations now default to cloud services when upgrading technology, and by 2024, 63% of companies are expected to have all or most IT infrastructure in the cloud. Enterprises are increasingly migrating on-prem applications to the cloud while small- to medium-sized businesses are adopting a cloud-native approach with many of the same goals: scalability, reliability, efficiency, security, and productivity.

Organizations once underestimated the security of cloud technology but, as cloud adoption grows exponentially, the concern should instead shift to using the cloud securely. Every month, thousands of data loss incidents happen in the cloud, leaving organizations at risk of non-compliance and the loss of sensitive data. According to Gartner research, 99% of cloud security failures are caused by human error.
Migrating to the cloud and managing infrastructure pose many challenges, but one of the most common yet underestimated issues is cloud misconfiguration. Often cited as the #1 cause of cloud data breaches and identified by the NSA as one of the top cloud security issues, a security misconfiguration can leave your company data easily accessible for threat actors.
Addressing cloud configuration and adopting a security plan to continually monitor for vulnerabilities can significantly reduce your organization’s security issues and strengthen your digital transformation.
The Security Threat of Misconfiguration
A cloud misconfiguration happens when an organization does not configure a cloud-based system or environment correctly, creating a vulnerability that can be exploited by a threat actor.
While no system can be 100% secure, just like no lock is 100% secure from lockpickers, a cloud misconfiguration Is essentially like leaving the front door unlocked.
Exploiting these cloud security vulnerabilities does not require sophisticated effort for cybercriminals, and the results can be devastating.
Most cloud data breaches happen due to cloud misconfigurations or human error, including high-profile breaches of sensitive data involving major companies, yet many breaches go unnoticed and unreported.
Fugue’s State of Cloud Security 2020 Survey found 84% of organizations are worried they have already been hacked and don’t know it, and 92% are concerned they are vulnerable to a major cloud misconfiguration data breach.
What our survey reveals is that cloud misconfiguration not only remains the number one cause of data breaches in the cloud, the rapid global shift to 100% distributed teams is creating new risks for organizations and opportunities for malicious actors.
Phillip Merrick, Fugue CEO
Here are just some recent cloud security breaches caused by misconfiguration:
- Capital One had a data breach in 2019 involving 100 million cardholders and credit applicants with Social Security numbers and linked bank account information exposed. The attacker exploited a misconfigured firewall and gained access to files stored in an AWS database. The breach occurred in March and was discovered four months later by an external security researcher.
- In 2019, the Defense Department had sensitive travel records compromising personal information of military and civilian personnel exposed due to an unspecified misconfiguration.
- The Defense Department also had databases exposed through misconfigured Amazon S3 buckets in 2017. Exposed data included classified information from Army Intelligence and Security Command. The cloud breach happened when Booz Allen Hamilton, the world’s largest government contractor, left sensitive files on an unsecured, publicly accessible AWS server without so much as password protection.
- In 2017, 11GB of confidential and sensitive U.S. military health care personnel data, including active top-secret security clearance holders, was leaked due to a server misconfiguration of a publicly accessible database.
- 6 million Verizon customer accounts were exposed through unsecured S3 storage buckets in 2017.
- In 2022, Thomson Reuters had left three databases with at least 3TB of sensitive data exposed including plaintext passwords for third-party servers and sensitive customer data.
- Microsoft exposed 2.4TB of business customer data due to a misconfigured endpoint that left multiple public buckets exposed in an incident dubbed the “Bluebleed Leak.”
- FedEx inadvertently exposed thousands of scanned documents in 2018 through an unsecured AWS cloud storage server. The leaked documents including applications for delivery of mail forms with customer information, driver’s licenses, and passports.
As these examples show, misconfiguration attacks can target not only companies of any size but also enable access to all types of sensitive data. As more organizations migrate to the cloud, the amount and type of sensitive data in the cloud grows.
The SANS 2022 Cloud Security Survey surveyed nearly 200 small, medium, and large businesses mostly in cybersecurity, banking and finance, technology, and education and found the majority have a variety of sensitive types of data in the cloud. The 2022 CSA Sensitive Data in the Cloud survey found most organizations (89%) host sensitive data and workloads in the cloud yet do not feel very confident in their own ability to protect this data. Just 31% of respondents were slightly confident and 44% were moderately confident in their ability.
Misconfiguration & Cloud Security Statistics
- Since 2021, cloud vulnerabilities have increased 28%, and there has been a 200% increase in the number of cloud accounts offered on the dark web (2022 IBM Security X-Force Cloud Threat Landscape Report)
- 80% of organizations using the cloud store sensitive data there (2022 Netwrix Cloud Data Security Report)
- 26% of files stored in the cloud contain sensitive data (McAfee 2019 Data Dispersion Cloud Adoption & Risk Report)
- 91% of cloud services do not encrypt data at rest which leaves data unprotected if the cloud provider is breached (McAfee)
- 79% of companies allow personal devices to access enterprise-approved cloud services and 1 in 4 have had sensitive data downloaded from the cloud to a personal, unmanaged device (McAfee)
- 79% of organizations had at least one cloud data breach in the past 18 months with 43% of businesses having 10 or more cloud data breaches (Ermetic State of Cloud Security 2021 Report)
- Organizations monitoring cloud services with Data Loss Prevention (DLP) experience an average of 45,737 incidents every month, but only 37% of companies have implemented DLP (McAfee)
How to Prevent Cloud Attacks: Common Cloud Misconfigurations & Solutions
Misconfiguration is a problem of human error and often comes down to:
- Inadequate oversight and controls,
- A lack of awareness of cloud security,
- An unmanageable number of interfaces and cloud APIs, and/or
- Negligent behavior of insiders.
One underlying cause of cloud misconfiguration is a misunderstanding of cloud security responsibilities. Many organizations fall victim to a misapprehension that the cloud service provider bears most of the burden of security.
While cloud service providers like Azure, AWS, and Google Cloud invest significant effort into the security of their services, these providers follow the shared responsibility model. This cloud security framework outlines where their security responsibilities end and the responsibilities of their customers begin.
Cloud service providers are responsible only for the security of the cloud infrastructure; organizations are responsible for the security of their assets and must take steps to protect their data and services.
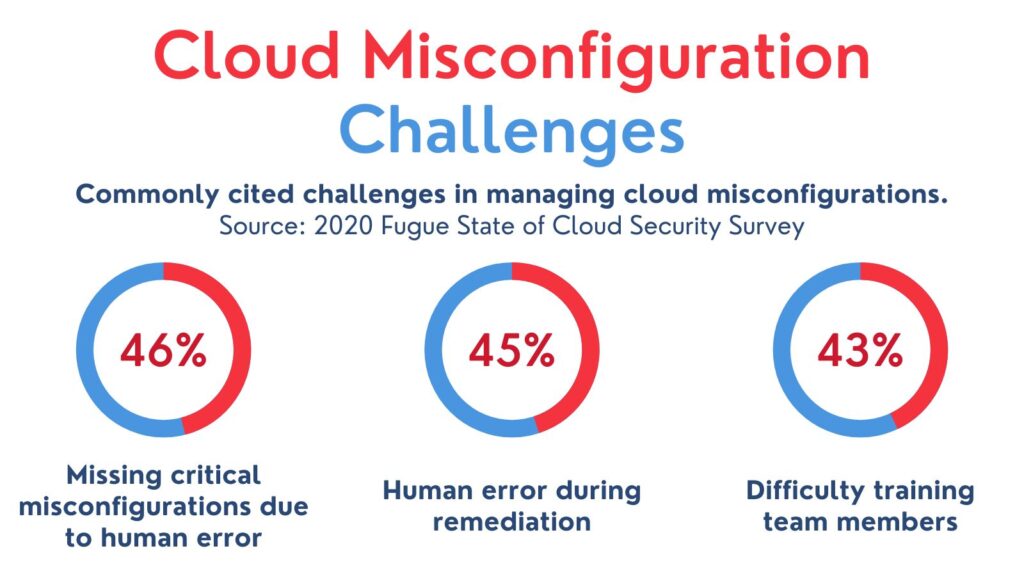
Cloud misconfigurations come in many forms. Some are as simple as failing to change default settings. Sometimes misconfiguration is the result of “misconfiguration drift” which happens when infrastructure is configured properly but over time, drifts away from the original setup. This usually happens when changes are made as needed, such as exceptions for a specific work requirement, without consistency, audits, or reverting temporary adjustments.
Cloud environments are becoming more complex and difficult to manage, especially with more organizations adopting a hybrid cloud strategy. This makes it even more crucial to understand how misconfigurations happen and adopt a strategy to prevent them.
Here are some of the most common cloud vulnerabilities caused by misconfiguration.
Unrestricted Inbound & Outbound Ports
Ports that allow internet access to resources pose a risk. Your team should be aware of all open ports with access limited to only the number of ports necessary. Ports that aren’t necessary should be restricted or locked.
Outbound ports can also be risky as they present an opportunity for lateral movement in your system, data exfiltration (unauthorized transfer, retrieval, or copying), and internal network scans. One of the most frequent misconfigurations is allowing outbound access to SSH or RDP. Application servers almost never need to SSH to other servers and do not need open outbound ports. Application servers should have outbound traffic restricted to only essential servers and applications.
Open Access to non-HTTP/HTTPS Ports
Port misconfigurations are common sources of misconfiguration attacks. When a port is opened to the internet, traffic must be encrypted and the port should only accept traffic from specific addresses. Only open ports you need and block ones you don’t from the internet to avoid easy access points for exploitation and brute-force attacks.
Improperly Configured or Disabled Monitoring and Logging
Strict logging protocols and regular monitoring of activity on your cloud platform can help identify other misconfigurations, suspicious activities, and unauthorized actions by employees and outside threats.
Any activity on your cloud platforms that could pose a security risk should be logged with continuous monitoring and automated alerts. Remember that alerts and flagged incidents are only useful if someone is paying attention; there must be someone responsible for regularly reviewing telemetry data. This can help identify and address questionable activities before they result in a breach or limit the impact of a data breach.
Storage Access Misconfiguration
There is often confusion about the difference between “authenticated” and “authorized” which leads to a common cloud misconfiguration. Users believing an “authenticated user” is one already authenticated within the organization or app are likely to configure storage bucket access to authenticated users only which leaves them completely exposed to public access. “Authenticated” simply means the user has credentials verified by AWS which is essentially all AWS clients.
Storage object access should be granted only to authorized users and essential data should be encrypted by default.
Excessive Privilege
A user is considered excessively privileged if more permissions are allowed than necessary to do their task. Cloud environments with overly permissive access make it easy for attackers to move laterally and exploit other cloud components. Common examples of excessive privilege or permissive access include:
- Sensitive APIs exposed without adequate controls
- Unpatched systems
- Excessively permissive network access rules
- Communication enabled between public and private resources
- External-facing ports exposed
- Legacy protocols enabled on a cloud host
X-Force Red penetration testing found 99% of cloud identities tested were excessively privileged.
Adhering to the least privilege principle is critical, although admittedly challenging. DevOps and security teams have a tendency to grand more privileges than needed. Functionality and efficiency are often prioritized over security to ensure teams can work uninhibited without slowing down business processes, but most granted permissions are not used and make lateral movement easier.
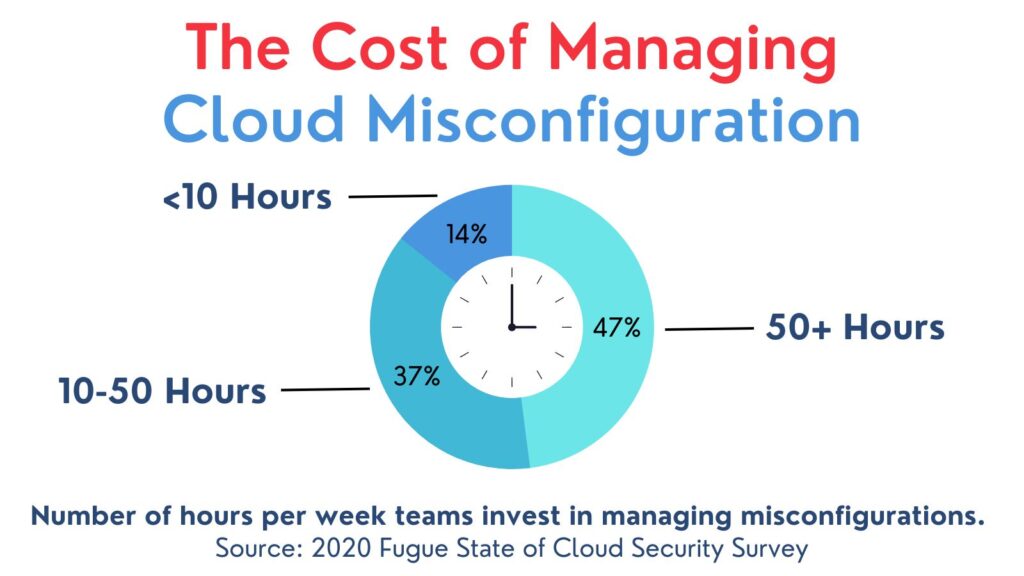
Default Credentials
It’s common for development teams to use default credentials for authentication. Not only are default credentials known by many people, including former employees, they are usually easy to guess.
Along with different configuration files for different development environments, there should be a process in place to avoid default credentials from being used in production environments.
Dangling DNSs (Subdomain Hijacking)
Subdomain hijacking happens when a subdomain name is changed or deleted from the virtual host (such as AWS) without addressing the associated CNAME entry from the Domain Name System (DNS). When an attacker finds the unused subdomain, it can be registered with the hosting platform and users can be rerouted.
This cloud vulnerability is easily avoided by deleting DNS records when subdomains and domains are no longer used.
Provider-Specific Misconfigurations
Along with misconfigurations that apply to all cloud providers, there are cloud configurations specific to the service you use that may pose a security risk.
One of the most well-known examples? The default public access setting for Amazon S3 buckets.
Many high-profile cloud breaches have been caused by the same problem: unsecured AWS S3 buckets. Amazon S3 buckets can be used by organizations to efficiently host assets and back up files. They’re frequently used to store files that are frequently accessed by internal teams and S3 buckets are easy and quick to set up. This also makes it easy for a misconfiguration to happen.
When S3 storage buckets are misconfigured, they can be publicly available with the ability to modify files and permissions. This introduces an even greater vector for malicious attacks.
In 2021, AWS S3 or Amazon Simple Storage Service alone accounted for 60% of breaches according to Paolo Passeri who tracks incidents caused by cloud misconfigurations.
After dozens of high-profile leaks, AWS has made changes to its default settings to reduce the chances of organizations accidentally making S3 storage buckets public, but misconfiguration is still common.
Other common AWS misconfigurations include a AWS CloudTrail configuration changes rule that, if disabled, prevents configuration changes from being recorded and monitored and the Amazon EBS App-tier EBS encrypted rule which, is not enabled, leaves data stored in AWS EBS volumes attached to app-tier ECS instances exposed.
Cloud Configuration Alone Isn’t Enough
Misconfigurations are one of the greatest cloud computing vulnerabilities for your organization. Even when cloud environments are configured correctly, configuration drift means over time, configurations are likely to change and become inconsistent, potentially exposing your organization to a devastating data breach or malicious attack.
It isn’t enough to set configurations properly the first time; your organization needs rigorous auditing of cloud configurations and solutions to monitor and remediate misconfigurations.
Don’t make the mistake of overlooking the human factor in cybersecurity. Your employees and contractors are one of your greatest assets, but they need the right training, security protocols, and support to not only do their jobs but maintain security in the cloud.
Is your organization overwhelmed by cybersecurity efforts? Or do you just need some help to free up resources and respond quickly and effectively to incidents? The cybersecurity experts at Infracore are here to help. Our security services include cybersecurity training, network security, multi-factor authentication, security audits, and more to make sure your organization has the best defense possible to cyber threats. Contact our team today to learn more.